Types of Phishing Attacks Every Business Should Know
Every year, hackers upgrade their tricks, but phishing still tops the charts. According to Verizon’s Data Breach Investigations Report, over 90% of data breaches start with a phishing attack.
What used to be sketchy emails full of spelling errors has now turned into smartly crafted messages, cloned websites, fake social media accounts, and even AI-generated voices that sound eerily real. The goal is always the same: to make you trust what you shouldn’t.
In this blog, we’ll look at how phishing attacks have evolved and uncover the different types of phishing attacks businesses face today, from email traps and text scams to deepfake calls. Understanding these cybersecurity threats isn’t just about awareness; it’s about staying two moves ahead of the attacker.
What is a phishing attack?

Phishing is a social engineering cyber-attack where attackers impersonate trusted entities, like banks, colleagues, or official platforms, to steal sensitive information such as passwords, credit card details, or corporate credentials.
It’s one of the most common initial attack vectors in breaches today, accounting for nearly 36% of all data breaches worldwide (Verizon DBIR 2024). The reason it works is simple: technology may evolve, but human behavior remains predictable.
Attackers exploit psychological triggers: urgency, curiosity, fear, and trust. A fraudulent email warning you that “your account will be suspended in 2 hours” or a fake Microsoft login page urging “immediate password verification” both rely on emotional manipulation, not technical skill.
Unlike malware or brute-force exploits, phishing attacks target people, not systems. They bypass firewalls and endpoint defenses by convincing users to open the door themselves. That’s what makes phishing both timeless and dangerous: it weaponizes trust in human communication.
Why Knowing the Types of Phishing Attacks Matters

For businesses, understanding the types of phishing attacks is not about theory; it’s about operational resilience. The better your teams recognize how these attacks work, the faster they can detect, contain, and neutralize them before any damage is done.
Effective security awareness training relies on real-world phishing scenarios. When employees learn to identify spoofed email domains, look-alike URLs, or fake MFA prompts, they become your first layer of defense, a human firewall that stops threats before they reach critical systems.
At a broader level, this awareness drives faster incident response. Security teams can flag a spear-phishing or business email compromise (BEC) attempt within minutes, preventing credential theft, financial loss, or data exposure.
For leadership, this knowledge builds confidence. When executives, partners, and customers understand phishing risks, your ecosystem becomes collectively stronger, because resilience in cybersecurity isn’t just built on tools. It’s built on informed people.
Most common types of phishing
Phishing has evolved far beyond deceptive emails. Modern attackers use multiple vectors, from text and voice to cloned websites and deepfake personas, to breach trust at every digital touchpoint. Below are the most common types of phishing attacks targeting organizations today.
1. Email Phishing

Over 90% of successful cyberattacks begin with a phishing email, according to the Cybersecurity and Infrastructure Security Agency (CISA). That makes email phishing the single most exploited entry point for attackers across industries.
In a typical campaign, cybercriminals send emails that appear to come from trusted sources, internal departments, vendors, or even global brands, to steal credentials, plant malware, or gain unauthorized access. These messages often use legitimate-looking domains, familiar branding, and emotional triggers like urgency or fear to push recipients into instant action.
For example, an employee in the finance team might receive an email marked “Urgent: Invoice Payment Required.” The message carries a realistic sender address, complete with the supplier’s logo and signature. Once the attached PDF is opened, malicious code silently installs a remote-access trojan, granting attackers entry into the corporate network.
Email phishing has evolved far beyond spam. Attackers now use encryption, AI-generated text, and compromised legitimate accounts to bypass even advanced filters, making security awareness and incident response more critical than ever.
Types of email phishing
- Deceptive Phishing: Generic mass emails impersonating popular brands to harvest user credentials.
- Spear Phishing: Personalized, research-backed emails targeting specific employees or departments.
- Whaling (CEO Fraud): Focused on top executives, often exploiting financial or approval workflows.
- Clone Phishing: A legitimate email is copied and resent with malicious attachments or altered links.
- Business Email Compromise (BEC): Attackers impersonate executives or vendors to request fund transfers or confidential data.
- Attachment-Based Phishing: Delivers malicious payloads through common file types like PDFs or Excel sheets.
- Link Manipulation / URL Phishing: Uses deceptive links — such as subtle domain misspellings — to redirect victims to fake login pages.
- HTTPS / SSL Phishing: Fraudulent websites use legitimate HTTPS certificates to appear authentic and gain trust.
2. Deep fake phishing
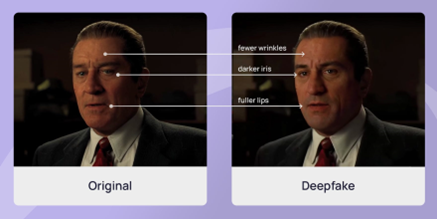
Deepfake phishing is one of the fastest-growing phishing attack types worldwide. A 2024 Symantec report found a 300% rise in AI-generated voice and video impersonation, proving how artificial intelligence is transforming social engineering. Attackers now use synthetic media to create voices and faces that look and sound exactly like real executives.
Unlike typical email phishing, these scams exploit trust and urgency through realistic audio or video deepfakes. For example, a finance manager might receive a video call from what appears to be the CEO, urgently requesting an overseas transfer. The tone, expressions, and background seem authentic — but the person doesn’t exist.
This new wave of AI phishing bypasses filters and policies because it manipulates perception, not software. To counter it, companies need executive verification protocols, such as multi-step approvals, callback validation, and AI-driven detection tools that analyze voice and facial anomalies before action is taken.
Types of deep fake phishing
- Voice Phishing (Vishing): Uses AI-generated or recorded voices to imitate executives or service providers.
- Video Deepfakes: Pre-recorded or live-streamed fake videos replicating known individuals.
- Synthetic Identity Phishing: Combines real and fabricated data to build credible digital identities.
- AI-Generated Email Phishing: Uses generative AI to write flawless, hyper-personalized phishing messages at scale.
3. Spear phishing

Spear phishing focuses on specific individuals instead of mass audiences. According to the 2024 Verizon Data Breach Investigations Report, nearly 30% of breaches begin with a targeted phishing attempt, showing how personalization has become the hacker’s strongest weapon.
For example, an HR head might receive a well-written email from a “recruitment partner” asking to verify employee records. The message uses the company’s logo, tone, and internal phrasing — but the link leads to a cloned site that steals credentials.
Because these attacks look authentic, they often bypass filters. Businesses need AI-based threat detection and continuous awareness training to spot the subtle cues — because in spear phishing, the most dangerous click is the one that feels safe.
Types of spear phishing
- Vendor / Supplier compromise: Attackers spoof or hijack a supplier’s account to send fraudulent invoices or payment requests.
- Credential harvesting: Personalized emails that direct victims to cloned login pages to capture corporate credentials and MFA tokens.
- Attachment-based spear phishing: Tailored messages carrying malicious documents (Macro, PDF exploits) designed to drop backdoors on targeted hosts.
- Link-based / URL spoofing: Context-rich emails with look-alike URLs or shortened links that redirect to convincing phishing sites.
- Account takeover preludes: Targeted attempts that gather just enough personal detail to enable a later account takeover (password reset, SIM swap).
- Business Email Compromise (targeted BEC): Focused impersonation of internal roles to manipulate approval workflows or request confidential files.
- Social media–enabled spear phishing: Attackers use data from LinkedIn/other profiles to craft hyper-relevant lures (job offers, project follow-ups).
4. Clone phishing

Clone phishing is a common and effective email technique where attackers replicate a legitimate email and swap its links or attachments for malicious ones. Phishing volumes remain high; the Anti-Phishing Working Group recorded over 1,000,000 phishing attacks in Q1 2025, and clone tactics are frequently used because they exploit existing trust in familiar messages.
For example, a user may receive a perfect copy of a past vendor invoice email with the original subject and formatting; the attached PDF looks genuine but contains a hidden macro that installs a backdoor when opened. Because the message feels familiar, recipients are far more likely to open the attachment or click the link.
Common variations include thread hijacking (inserting malicious content into an active email thread), attachment-swapped clones (legitimate attachment replaced with malware), and URL-replaced clones (original links replaced with look-alike domains). Detect these by validating sender domains, checking digital signatures, and confirming attachments via an independent channel before acting.
Types of clone phishing
- Thread hijacking: Attacker inserts malicious links or attachments into an active, trusted email conversation to exploit ongoing trust.
- Attachment swap: A previously safe message is resent with the original attachment replaced by a malicious document (macro, trojan).
- URL replacement: Legitimate links are swapped for look-alike domains or shortened URLs that redirect to phishing pages.
- Account compromise clones: Emails sent from a compromised internal or vendor account, making the cloned message appear fully authentic.
- Reply-chain cloning: Attacker replies to a real message with a near-identical response that includes a fraudulent payment or update link.
- Invoice/payment clone: Past invoices are duplicated with modified payment instructions or beneficiary details to redirect funds.
- Policy/HR doc clone: Internal policy notices or HR updates are cloned with malicious attachments to target employee systems.
- Timed replays: Old legitimate messages are replayed at strategic times (quarter-end, payroll) with swapped links to increase the chance of action.
5. Dropbox/Google Drive Phishing

Attackers increasingly use legitimate file-sharing platforms like Google Drive, Dropbox, and OneDrive to host phishing pages and bypass filters; Microsoft observed a marked rise in campaigns that misuse file-hosting services for identity phishing. A focused study also recorded a 201.5% increase in phishing using Google Slides links over a recent six-month window, underscoring how attackers weaponize trusted collaboration tools.
In a typical attack, an employee receives a message that looks like a platform notification: “A file has been shared with you,” with a genuine Google or Dropbox URL. For example, a project manager clicks a shared Google Slides link that opens a convincing sign-in prompt; the attacker captures the credentials and uses the account to spread further malicious links from a trusted sender. Because the link originates from a legitimate domain, cloud storage phishing often evades standard URL filters and basic email protections.
Defend by enforcing least privilege access, enabling cloud provider security controls (DLP, conditional access, MFA), and training staff to verify shared links via out-of-band channels before signing in. Monitor for unusual sharing patterns and treat any unsolicited shared document, especially those that urge credentials or downloads, as high risk.
Types of Dropbox / Google Drive Phishing
- Fake shared document alerts: Attacker sends a forged “File shared with you” email linking to a malicious sign-in page.
- Embedded link phishing: Legitimate-looking documents hosted on Google Drive or Dropbox contain redirect links to external phishing sites.
- Fake login portals: Cloned Microsoft 365 or Google Workspace login screens embedded within cloud documents to harvest credentials.
- Comment-tag phishing: Attackers tag users in document comments containing malicious URLs or “access requests.”
- Compromised account sharing: A legitimate user account is hijacked and used to share malicious files with internal teams.
- Storage quota/access warning scams: Fake Drive or Dropbox alerts claiming the account will be locked or storage is full, prompting users to “verify.”
- Collaboration invite phishing: False invites to shared folders or projects that lead to credential-stealing landing pages.
- API abuse attacks: Malicious third-party apps requesting OAuth permissions through Drive integration to gain persistent access.
Best Practices to Protect Your Company from Phishing Attacks
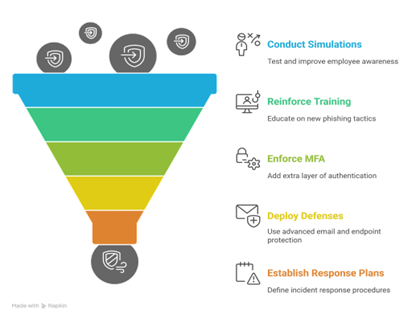
Even the most advanced security tools can’t compensate for a single human click. A strong defense against phishing isn’t built on technology alone; it’s built on prepared people, defined processes, and adaptive systems working together.
1. Conduct continuous phishing simulations
The most effective awareness isn’t theoretical, it’s experiential. Regular phishing simulations help employees recognize evolving lures in real time. At Alliance Pro, our internal security teams use these simulations to assess user response patterns, update training content, and measure awareness maturity across departments.
2. Reinforce security awareness training
Awareness fades if it isn’t sustained. Real-world case studies, incident breakdowns, and interactive modules keep employees alert to new tactics like AI-generated emails or drive-based phishing. When users understand why an email looks suspicious, they stop relying on instinct and start responding with insight.
3. Enforce multi-factor authentication (MFA)
Even if credentials are compromised, MFA acts as a critical barrier. Enforce it across cloud applications, VPNs, and collaboration tools to limit the blast radius of credential theft.
4. Deploy advanced email and endpoint defenses
Use AI-driven email gateways, DMARC/DKIM/SPF, and sandboxing to flag spoofed messages and detonate malicious attachments safely. Pair that with endpoint monitoring to detect post-click behavior early.
5. Establish clear incident response playbooks
A phishing response plan defines who acts, how fast, and in what order. At Alliance Pro, simulations often extend to blue-team exercises, testing how quickly IT and security units isolate compromised accounts, revoke sessions, and initiate post-incident reviews.
6. Verify requests through alternate channels
Always confirm unexpected financial or data requests through direct communication or call-back verification, especially for high-value or time-sensitive approvals.
7. Apply the principle of least privilege
Restrict access to essential systems and data. Fewer permissions mean fewer attack surfaces if a user account is compromised.
8. Keep your ecosystem patched and observed
Regular patching, vulnerability scanning, and SIEM-based threat monitoring close the gaps that phishing campaigns depend on. The goal isn’t to avoid every email, it’s to build an environment resilient enough to withstand one mistake.
The Future of Phishing Defense
Phishing is evolving faster than most defenses. With AI-generated attacks, deepfake impersonations, and cloud-based phishing campaigns on the rise, organizations can no longer rely on reactive measures. The future of phishing prevention lies in proactive simulation, continuous user awareness, and adaptive AI-driven security that learns as fast as attackers do.
At Alliance Pro, we believe resilience begins with readiness, preparing your people, your systems, and your response strategy before the next phishing email lands. Because in cybersecurity, the strongest defense isn’t luck. It’s practice, precision, and partnership.
Ready to make your organization phishing-resilient? Let’s start building your defense where it matters most, with your people.








Leave a Reply